Cyber Breach Readiness Ensures you are prepared for and can respond to a cyber breach
Are you prepared for a cyber breach?
Organisations are always at risk of a cybersecurity incident. No business, large or small, is immune from threats and data breaches.
If you are not ready for a breach it leads to operational downtime, damage to reputation, or completely going out of business.
Risks and concerns you face if you’re unprepared
Knowing how to detect a cybersecurity breach and having a response plan in place are fundamental for any organisation.
Failing to prepare, can result in serious cyber attacks and longstanding problems in your organisation.
Package Approach
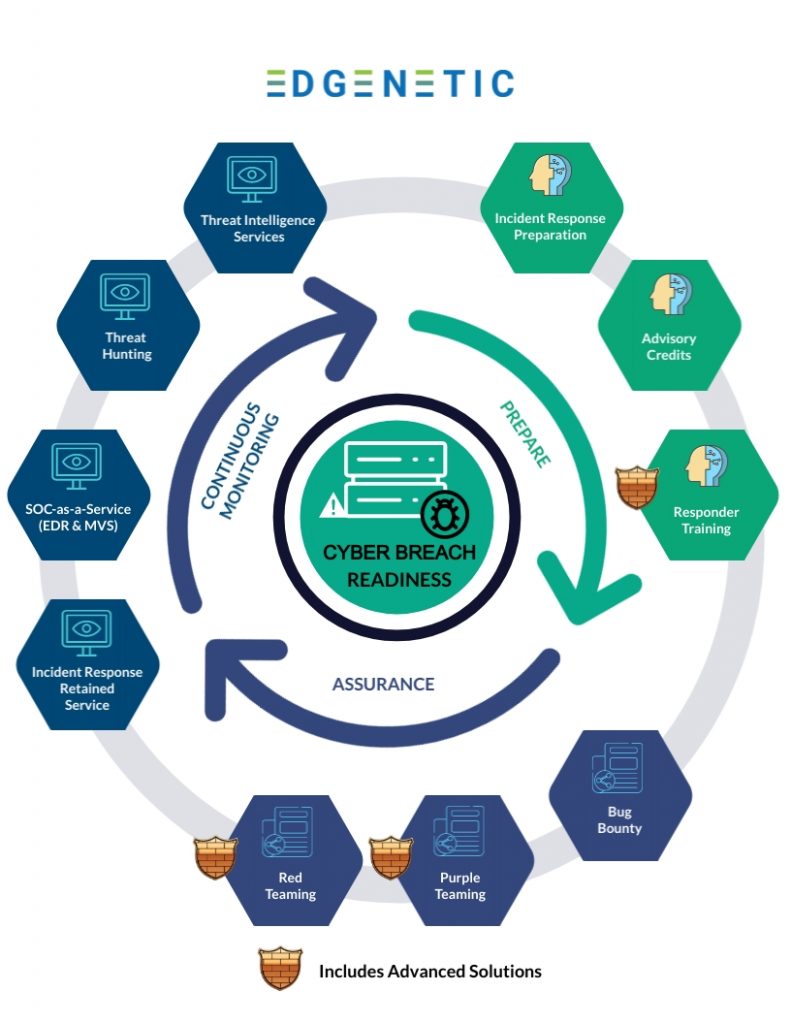
This package has three core phases:
Prepare
• Reviews the effectiveness of the security and technical configuration controls of your technology systems. Prepares your people, processes, and documentation to ensure you can respond and recover from a cyber breach.
Continuous Monitoring
• Provision of services and cyber expertise that supports detection, protection, and response capability.
Assurance
• Provision of technology-based security services combined with cybersecurity expertise to continuously test and assure your posture.
Choose our Cyber Breach Readiness package
This package ensures that the correct processes, people, and technology are in place and have been tested to ensure a high level of confidence your organisation can respond to a cyber breach.
The package is split into two offerings, Baseline and Advanced, select your package below.

Technical Account Manager (TAM)
A Technical Account Manager (TAM) is your first line of engagement and ensures you are led through the delivery of work streams required.
The TAM works with your team to drive priorities, deliver value, and align with your business concerns, risks, and drivers. Pivoting between LRQA Nettitude’s operational teams and your staff they liaise regularly, helping to schedule work, and ensure delivery.
Cyber Maturity Assessment
Quickly understand your organisation’s security posture to take risk-based decisions on improvement planning and budget and resource allocation.
Conducted through workshops, this service asks insightful and valuable questions that will enable a clear view of your cybersecurity needs and identifies any gaps and areas for improvement. Benchmarked against industry standards this assessment provides an external review and assurance of your organisation’s cyber maturity.
Advisory Credits
Advisory Credits provide you with access to cyber expertise when you need it most. We can assist you with advisory consulting through to technical and cyber expertise in all fields.
Incident Response Preparation
Assessment & Preparatory
Our team of experienced professionals can help mature and improve your organisation’s response plan through thorough planning and engaging tabletop exercises. From malware and ransomware to extortion and fraud, we ensure that you are ready to handle any attack thrown at you.
Security Configuration Review
As part of this service, we assess your backup strategy, cloud configuration and complete a Network Security Review.
Bug Bounty
You pay us when we find issues, based on their criticality. We are always looking (same as the bad guys) and we will spend more time and resources looking deeper and wider into your systems that can be covered in a standard penetration test.
Incident Response Service
EDGENETIC provides Incident Response (IR) service tailored to suit your needs and threats your organisation could be facing.
We provide a full range of tactical and strategic solutions tailored to your environment and organisation to prepare, practice, and respond swiftly in the event of a cyber-attack, helping you resume normal business operations quickly.
Managed Detection and Response
In today’s world, endpoint protection is becoming a necessity to be able to reduce the likelihood of an adversary attacking your organisation, leading to a data breach, Ransomware, or other malicious action against you.
Endpoint Detection and Response (EDR) solutions are configured to be able to defend and alert against these malicious activities, helping to reduce the time to detect and respond to an incident.
Managed Vulnerability Scanning
Our Managed Vulnerability Scanning Service deploys a leading cloud-based vulnerability scanning and management technology to be able to identify, investigate, prioritise, mitigate, and respond to vulnerabilities within your environment and attack surface.
Understanding your risks as the number of vulnerabilities increases is critical in the current threat landscape. Managed Vulnerability Scanning is a fundamental component of any security testing programme for identifying existing or new vulnerabilities and misconfigurations across your systems.
LRQA Nettitude MVSS services have multiple customisable options tailored to fit your organisation that aid cyber maturity and risk-based methodologies to help you remediate and stay on top of critical issues and vulnerabilities that could leave you exposed.
Threat Intelligence Services
ThreatWatcher service provides a managed assessment using advanced reconnaissance and analytics to identify previously unknown threats that could be used against your organisation in a cyberattack.
Security intelligence from ThreatWatcher can highlight weaknesses in your user education and help to identify your digital attack surface like never before. Once understood the recommendations from the assessment can supercharge risk reduction across your organisation and help drive your organisation to an intelligence-led security strategy.

Technical Account Manager (TAM)
A Technical Account Manager (TAM) is your first line of engagement and ensures you are led through the delivery of work streams required.
The TAM works with your team to drive priorities, deliver value, and align with your business concerns, risks, and drivers. Pivoting between LRQA Nettitude’s operational teams and your staff they liaise regularly, helping to schedule work, and ensure delivery.
Cyber Maturity Assessment
Quickly understand your organisation’s security posture to take risk-based decisions on improvement planning and budget and resource allocation.
Conducted through workshops, this service asks insightful and valuable questions that will enable a clear view of your cybersecurity needs and identifies any gaps and areas for improvement. Benchmarked against industry standards this assessment provides an external review and assurance of your organisation’s cyber maturity.
Advisory Credits
Advisory Credits provide you with access to cyber expertise when you need it most. We can assist you with advisory consulting through to technical and cyber expertise in all fields.
Incident Response Preparation
Assessment & Preparatory
Our team of experienced professionals can help mature and improve your organisation’s response plan through thorough planning and engaging tabletop exercises. From malware and ransomware to extortion and fraud, we ensure that you are ready to handle any attack thrown at you.
Security Configuration Review
As part of this service, we assess your backup strategy, cloud configuration and complete a Network Security Review.
Bug Bounty
You pay us when we find issues, based on their criticality. We are always looking (same as the bad guys) and we will spend more time and resources looking deeper and wider into your systems that can be covered in a standard penetration test.
Incident Response Service
EDGENETIC provides Incident Response (IR) service tailored to suit your needs and threats your organisation could be facing.
We provide a full range of tactical and strategic solutions tailored to your environment and organisation to prepare, practice, and respond swiftly in the event of a cyber-attack, helping you resume normal business operations quickly.
Managed Detection and Response
In today’s world, a SIEM solution combined with endpoint protection is becoming a necessity to be able to reduce the likelihood of an adversary attacking your organisation, leading to a data breach, Ransomware, or other malicious action against you.
SIEM and Endpoint Detection and Response (EDR) solutions are configured to be able to defend and alert against these malicious activities, helping to reduce the time to detect and respond to an incident.
Managed Vulnerability Scanning
Deploys a leading cloud-based vulnerability scanning and management technology to identify, investigate, prioritise, mitigate, and respond to vulnerabilities within your environment.
Failing to understand and remediate the vulnerabilities within your environment could present an attacker with the opportunity they need to gain access to your systems.
Advanced Threat Intelligence Services
ThreatWatcher service provides a managed assessment using advanced reconnaissance and analytics to identify previously unknown threats that could be used against your organisation in a cyberattack.
Security intelligence from ThreatWatcher can highlight weaknesses in your user education and help to identify your digital attack surface like never before. Once understood the recommendations from the assessment can supercharge risk reduction across your organisation and help drive your organisation to an intelligence-led security strategy.
Red Teaming
We simulate threat attack paths to your assets (not just compromising your perimeter). This tooling allows the Red Team to simulate real-world threats against your organisation in the closest manner to a real attack.
A Red team creates in-depth attack paths that mimic a wide range of sophisticated scenarios and inform you clearly of the current assurance levels around a cyber-attack.
Purple Teaming
Purple Teaming exercises simulate specific attack scenarios to ensure your organisation is prepared to detect and respond in the real world. This is conducted as a joint exercise by the LRQA Nettitude Red Team (attackers) and Blue Team (defenders). This will improve your organisation’s security posture and increase resiliency to sophisticated attacks.
Managed Threat Hunting
The world of technology moves at a rapid pace and as such there are new techniques used by attackers to compromise organisations which may evade traditional detection solutions.
Our Threat Hunt-as-a-Service is provided using a mixture of sophisticated technology and highly certified threat hunters to provide assurance and identify whether your organisation is currently compromised, or even where historic compromise activity has occurred.
It understands the impact of any discovered breach and provides actionable guidance on the next steps to respond to and eradicate the threat.

Ransomware & Malware
How safe is your organization from a ransomware threat? Ensure you are always prepared for a ransomware or malware attack with this package.

Cyber Breach Readiness
Is your organization prepared for a cyber breach? This package prepares your organization and ensures you can respond to a breach.

Supplier & Third-Party Risk Management
Can you trust your supplier’s and third-parties cybersecurity? Select this package for complete assurance, governance, and risk management of your supply chain.

Employee Security & Training
Concerned about how to protect against threats that target employees? This package will secure and train employees while monitoring the threats they face.

Penetration Testing Remediation
Penetration Tests have identified your weaknesses, but do you know how to remediate vulnerabilities? Select this package to ensure remediation is fully executed.

New Technology Cyber Risks
Concerned that moving to new technology will increase cyber risks? Choose this package for assurance that new technology is secured and protected by experts.

Technical Legacy Debt
Do you know legacy software systems can expose you to cyber threats? Ensure your systems are safe with this package to manage and secure legacy systems.
Develop a Cybersecurity Programme
Can you prevent, withstand, and recover from cyber incidents? This package builds a cyber strategy equipping you against evolving threats.
