SOC-as-a-Service
Detection & Response for sophisticated threats
EDGENETIC is an award-winning cybersecurity organisation with unparalleled capability in delivering SOC-as-a-Service. Through our global Security Operations Centres (SOCs) we are able to deliver round the clock services that secure our clients, and detect and respond to sophisticated cyber-threats providing assurance that what matters most is protected.
Why use a Managed SOC?
In today’s interconnected world, it is increasingly difficult for organisations to protect their data, as technology continues to rapidly evolve and change the working practices of organisations and people. Organisations have typically responded by implementing security technology at strategic vantage points within the network infrastructure. Yet, despite this approach, companies are still being breached and data is being compromised.
A Managed SOC Service can provide a level of visibility and security that can be difficult to maintain in-house, both in terms of availability and expertise. Organisations that have limited resources can procure Managed SOC Services to manage their alerting, detections, and incidents. Alternatively, you can supplement an existing team, providing in-depth expertise and availability when you need it most.
The Cyber-threat Landscape is Evolving
The volume of cyber-attacks grows continually year-on-year. For organisations to maintain a strong security posture, they need to deliver round the clock security services. Attackers do not only act during core business hours, they attack organisations 24 hours a day, 365 days a year.
Security monitoring is a must in today’s business world with threats, cyber-attacks, and data breaches becoming a regular part of the global news. But where do you start implementing security services to combat these threats?
Not all companies can afford to set up, hire security experts and operate a mature Security Operations Centre that can protect against the ever-evolving security threat landscape.
With our Managed SOC-as-a-Service you benefit from an award-winning SOC, which includes the crucial technologies and experts critical to protecting against these threats.

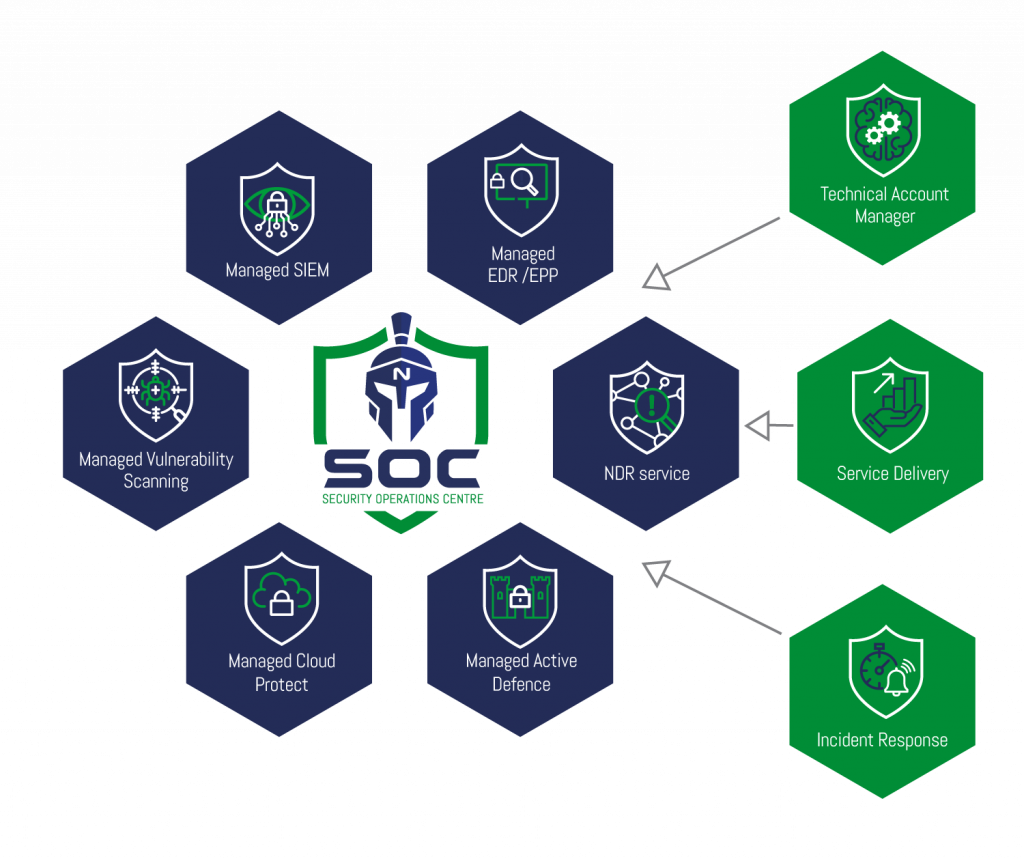
About LRQA Nettitude’s SOC-as-a-Service
Service Components
Whether you require a SIEM solution or a combination of tools and services to protect your entire organisation, LRQA Nettitude’s SOC-as-a-Service can be customised by selecting service components suitable to protect your environment and critical systems.
EDGENETIC’s SOC-as-a-Service utilises leading security
technology vendors, combined with automation and orchestration to deliver a robust & comprehensive Managed Security Service offering to suit your needs.
The flexible and component-based offerings can be selected or added to as your cybersecurity maturity evolves.
EDGENETIC has extensive experience in delivering robust and adaptable security monitoring services, giving you the confidence required on what’s important to you.
Service Features
EDGENETIC’s SOC-as-a-Service provides the most highly accredited expertise combined with Gartner Magic Quadrant leading security technology to deliver industry-leading protection for your organisation.
Our approach is proactive, and threat led; informed by our offensive and threat intelligence teams to shape our defensive stance and protect against the latest industry threats providing in-depth unrivalled detection and alerting capability where it is needed most.

EDGENETIC Security Operations Centre
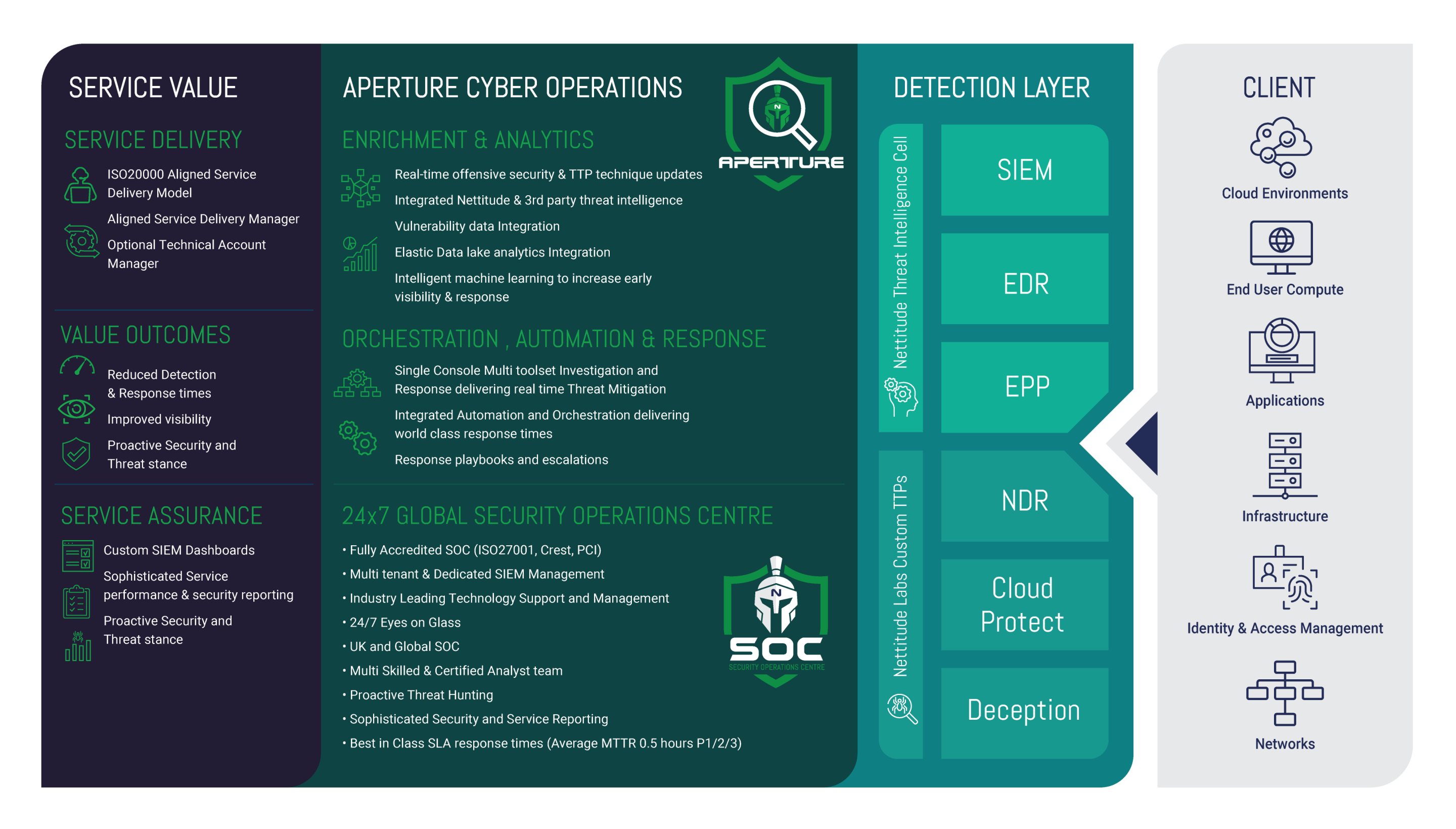
Aperture Cyber Operations
TheEDGENETIC SOC-as-a-Service provides advanced 24/7 monitoring and alerting to protect your business.
We use our custom developed Aperture Cyber Operations Management platform to provide enhanced automation, orchestration, and response capabilities to our SOC team. The Aperture Cyber Operations platform provides enrichment, analytics, integration, and intelligent learning to increase early visibility and response to cyber-threats in an evolving world.
- Real-time offensive security and TTP updates
- Integrated threat intelligence
- Intelligent elastic data learning
- Single console multi-tool investigation and response
- Integrated automation and orchestration
- Best in class alert and response service levels

Why use EDGENETIC’s SOC-as-a-Service?
EDGENETIC prides itself on delivering value-add services for our clients, many organisations can deploy and manage a reactive security monitoring technology, but to implement these technologies and then realise the returns on investment is difficult in an ever-evolving security landscape.
Our expertise and experience enable us to provide proactive, value-add services to our clients built on foundations across people, process & technology.
The Right People
SOCs rely heavily on having capable people that are trained and experienced in identifying threats. It is essential that the people in a SOC have a deep technical experience that allows them to think like an attacker, and review network traffic to identify security events. In addition, when incidents are identified, it is necessary to have a robust incident management program to ensure artefacts are preserved and mitigation activity can be actioned.
EDGENETIC’s deep understanding and experience of offensive attacks and ability to simulate sophisticated threat actors provides a firm knowledge base for our detection and response capabilities.
EDGENETIC’s SOC invests heavily in its most valuable asset, our staff. They are highly certified and continually developed through learning and certifications to ensure we stay on the leading edge of cyber defence operations.
Our skilled teams include security and technical staff, incident responders, service delivery managers, and technical account managers to provide an all-encompassing tiered delivery model that remains flexible whilst providing best in class security services.
Robust Processes
One of the most crucial aspects of a SOC is to have robust operating procedures and processes to govern and orchestrate the operational delivery and the detection and response lifecycles. In EDGENETIC’s experience, it is the quality of the SOC process that ultimately influences the overall SOC effectiveness.
Threat Modelling
It is essential that up front threat modelling and risk understanding is carried out in advance of setting up a SOC service. As part of this process, a thorough understanding of critical assets and attack surfaces is used to build out a strategic view of the organisation’s estate and digital assets.
A SOC must embrace both proactive and reactive processes to deliver the optimum level of visibility across an organisation’s estate. Reactive log review from strategic vantage points across an estate is critical to providing visibility across a monitored infrastructure. However, that alone will rarely suffice in today’s current threat landscape.
EDGENETIC proactively completes hunt initiatives across critical assets and through network data captures. By blending proactive and reactive processes together, EDGENETIC’s SOC provides a holistic security approach to prevent critical asset compromise and data exposure.
Use Cases and Orchestration
Understanding how attackers move laterally across a network is critical in detecting advanced threats. Determining what normal user behaviour is, and then deviations away from this is a critical component of an effective SOC.
EDGENETIC has extensive experience in building use cases and processes that allow us to identify and contain attacks at multiple stages of the cyber kill chain. Our orchestration and use cases are based around many common attack patterns, and allow us to respond to malware breakouts, remote access toolkits (RATs), Command & Control (C2), lateral movement, privilege escalation, and attempted data exfiltration.
Service Operation & Delivery
An Operational SOC performance can be hard to maintain without the right processes and procedures to ensure quality outcomes are delivered to the client. Most IT services within a company are governed and provided using industry-aligned standards like ITIL and ISO20000k.
EDGENETIC has a mature ITIL/ISO20000 aligned service operation and delivery framework. This ensures we manage, maintain, and deliver the best SOC services to our clients. We align and measure all our processes and performance in line with industry standards and continually investigate improvement opportunities.
The Best Technology
Having the right type of technology, that is fit for purpose and provides a rich data set to a security analyst, is essential in detecting and responding to cyber-threats. In today’s marketplace, there are many technologies to choose from. So, how do you know which is best for you?
Visibility
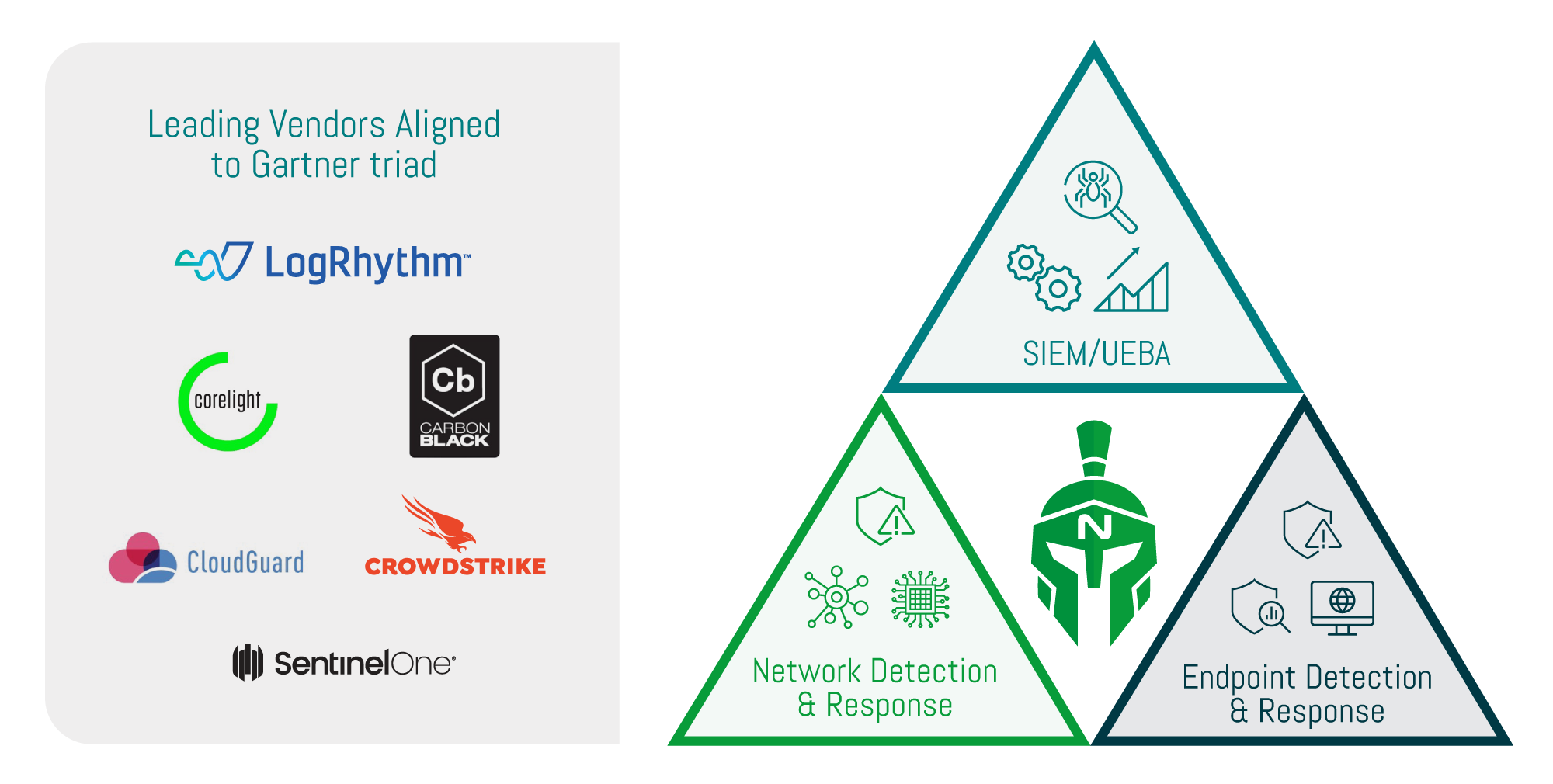
EDGENETIC have invested in and tested best of breed cybersecurity technologies across the industry. We only use technologies we have heavily tested in real-world scenarios that we can be sure provide the best protection possible.
These best of breed technologies are combined with EDGENETIC’s custom-developed Aperture Cyber Operations technology to ensure coverage and protection across all of the Gartner triad to ensure complete visibility of your environment.
Service Components & Capability


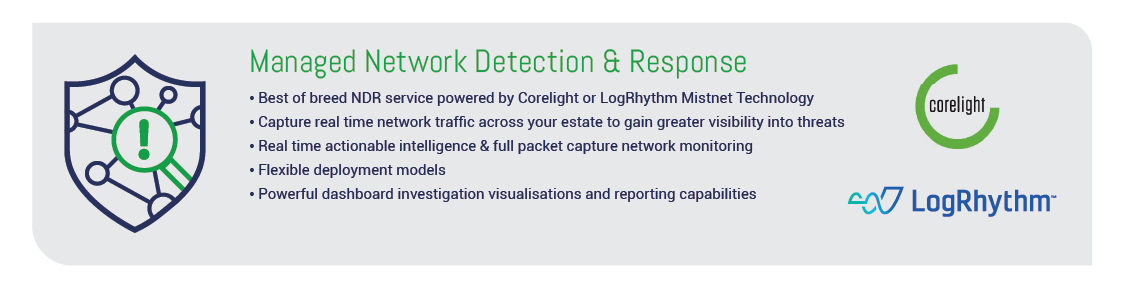




EDGENETIC Cyber Incident Response
EDGENETIC Cyber Incident Response Team – NCIRT
The EDGENETIC SOC provides a world-class Incident Response (IR) service powered by the EDGENETIC Cyber Incident Response Team (NCIRT) team, tailored to suit the needs and threats your organisation could be facing.
Using leading industry technology and certified experts, the NCIRT manages, contains, remediates, and reports on cyber incidents providing assurance when it is needed most.
The NCIRT team are highly certified and experienced in all aspects of cyber incidents and we follow and adhere to best practice industry guidance and standards from NIST, FIRST, SANS, NCSC and CREST.
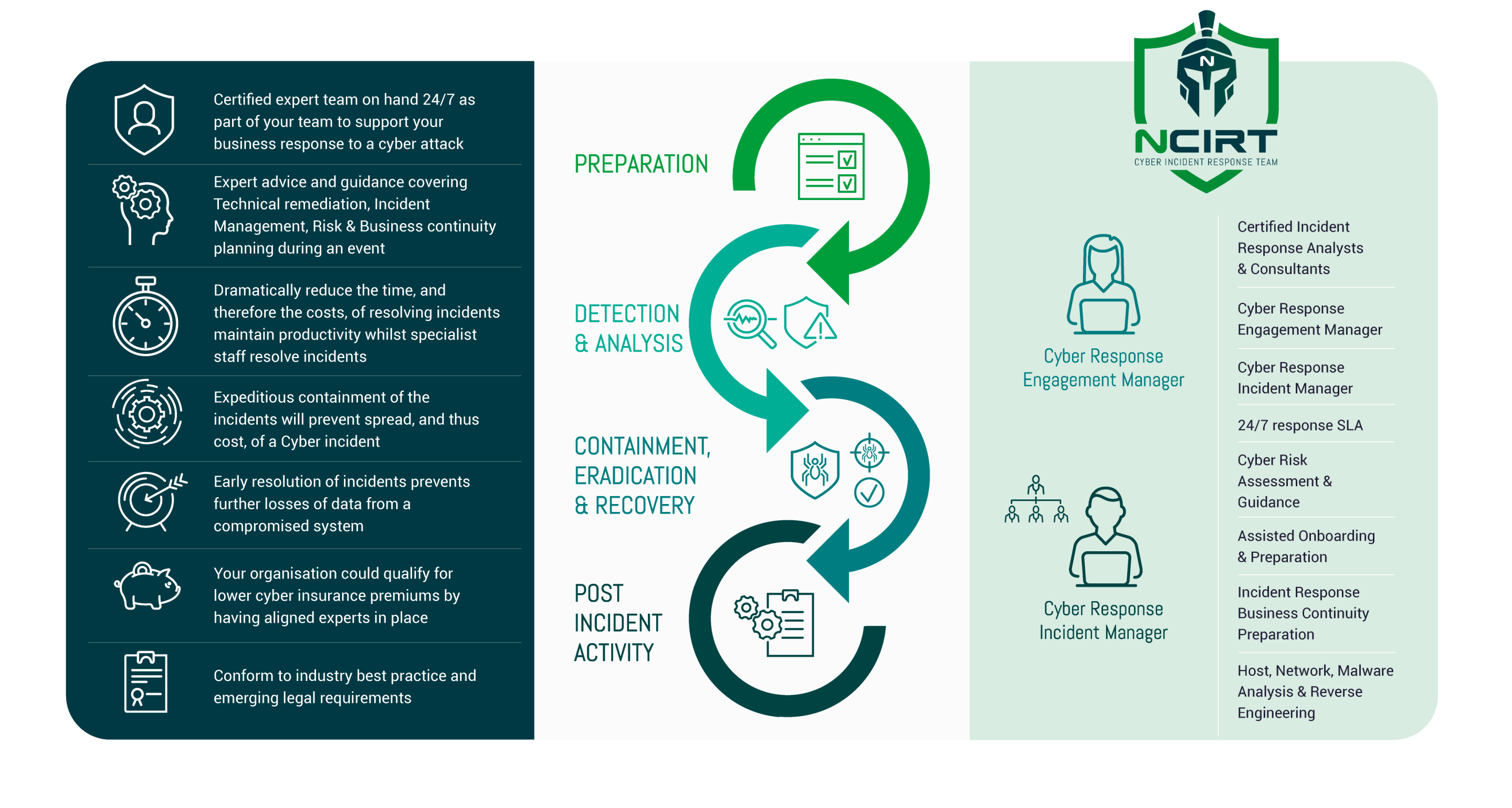
Incident Response Service Features
EDGENETIC’s Incident Response service provides the most highly accredited expertise combined with Gartner Magic Quadrant leading security technology to deliver industry-leading protection for your organisation.

