MANAGED NETWORK DETECTION & RESPONSE
MANAGED NETWORK DETECTION & RESPONSE
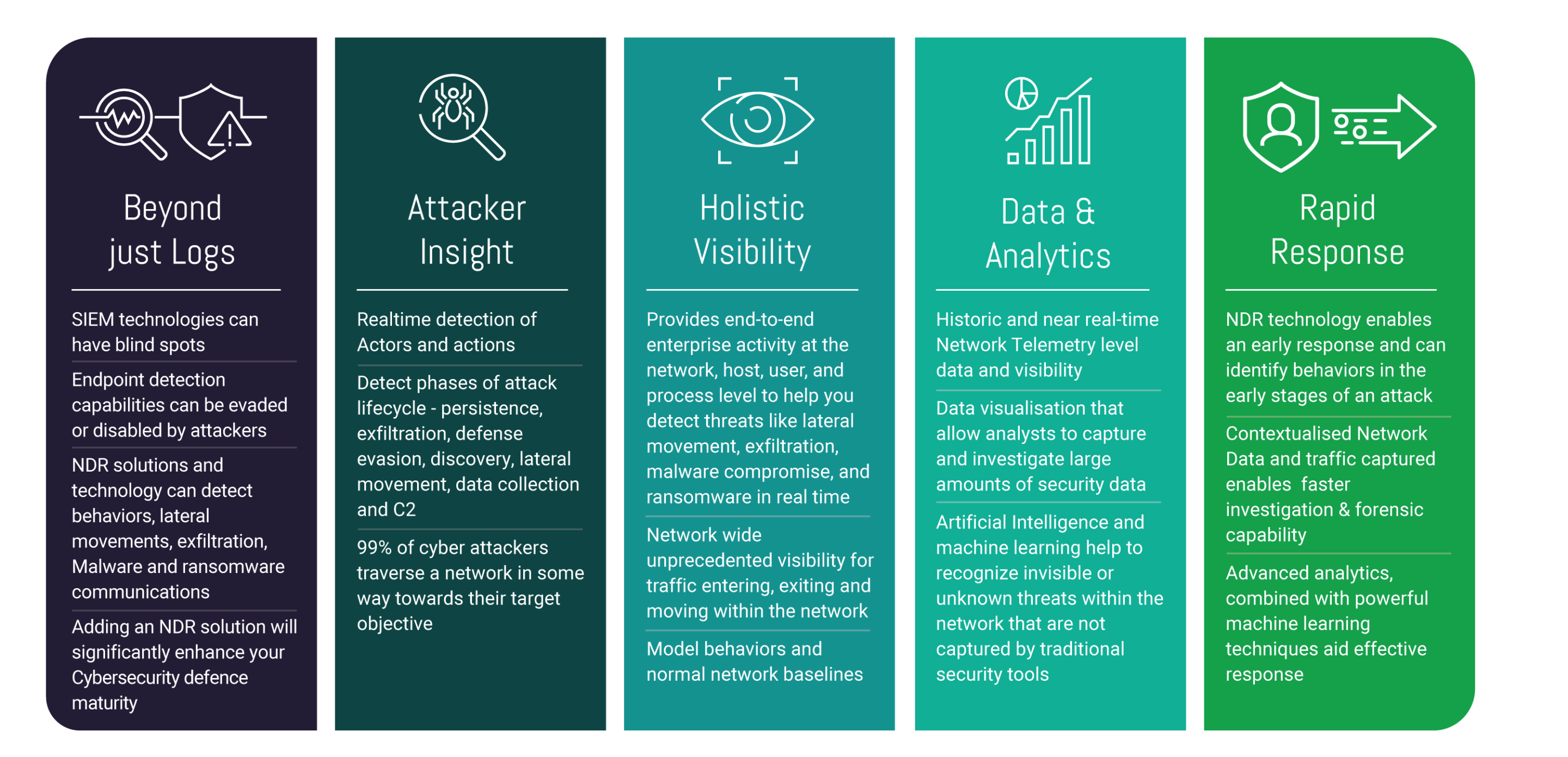
Network security & visibility needs more than just logs
A managed Network Detection and Response (NDR) service can provide a level of visibility and security that can be difficult to maintain in-house, both in terms of availability and expertise.
The EDGENETIC Managed NDR service can be utilised by organisations that have limited resources and expertise to assist with the provision, management, and monitoring of Network Detection and Response technologies, to provide world-class capability to protect your environment.
EDGENETIC is an award-winning cybersecurity organisation with unparalleled capability in delivering managed security services. Through our global Managed Security Operations Centres (SOCs) we deliver round the clock services that secure our clients and detect and respond to sophisticated cyber-threats, providing assurance that your organisation is protected.
What Is Managed NDR?
NDR technologies continuously monitor an organisation’s network to detect cyber-threats, anomalous behaviour, or malicious traffic using non-signature-based tools and techniques that provides real-time continuous monitoring and detection, combined with response and analysis capabilities.
Advanced NDR solutions provide complete visibility across all users, devices, and technologies connected to the network providing coverage across end-users, data centres, and cloud environments.
Network traffic is continuously monitored when entering, exiting, and moving within the network for unprecedented visibility utilising behavioural analytics and machine learning to detect cyber-threats and anomalous behaviour. This data is captured in real-time and used to detect and model against known adversary tactics, techniques, and procedures providing a holistic contextual network-wide visibility.
The importance of network detection and response is recognised as a key pillar of the Gartner SOC visibility triad. A common misconception is that Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) solutions sufficiently protect the enterprise environment. Yet, the widespread adoption of IoT, cloud computing, and digital transformation means that NDR is an increasingly important tool within the SOC visibility triad to combat sophisticated attackers.
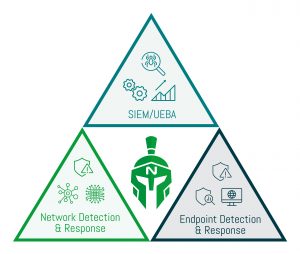
Benefits Of Managed NDR
A common misconception is that SIEM and EDR tools will provide sufficient protection against cyber-threats and attacks. These tools are a good start and form two corners of the SOC visibility triad. However, networks have become an increasingly valuable target with the widespread adoption of new technologies like cloud and IoT.
Adopting an NDR solution will significantly enhance your cybersecurity defensive stance whilst also ensuring your ability to defend against both sophisticated network attacks and highly organised threat actors.
Network Detection & Response Technologies
Corelight
Corelight delivers the most powerful network visibility solutions for cybersecurity professionals. It helps them understand network traffic and defend their organisations more effectively.
Corelight solutions are built on the Zeek framework (formerly known as ‘Bro’), the powerful and widely-used open-source network analysis framework that generates actionable, real-time data for thousands of security teams worldwide.
Zeek data has become the gold standard for incident response, threat hunting, and forensics in large enterprises and government agencies worldwide.
Corelight makes a family of network sensors (both physical and virtual) at every scale, that takes the pain out of deploying open-source Zeek by adding integrations and capabilities large organisations need.
Corelight Sensors extract more than 400 data elements from network traffic in real-time, using a format chosen by incident responders, for incident responders. The Corelight Sensor is zero-maintenance and fine-tuned for enterprise performance at scale providing unrivalled network detection capability.

MistNet by LogRhythm
MistNet NDR by LogRhythm was designed to provide accurate and real-time detection of ransomware, lateral movement, exfiltration, malware compromise, and other threats.
While other NDR solutions rely solely on machine learning applied to single streams of data to detect network security issues, LogRhythm uses hybrid analytics that combines machine learning, rules-based detection, and threat intelligence to analyse network, user, and host activity.
This holistic approach provides a true representation of all actors and their activity within the enterprise domain and reduces false positives by over 90 per cent.
The built-in MITRE ATT&CK engine of MistNet NDR provides smart hunting of tactics, techniques, and threat groups across multiple attack vectors. Analysts are provided with an easy-to-understand security ‘narrative’ detailing, in real-time, known ATT&CK tactics, techniques, and threat group signatures.
The powerful threat detection and hunting capabilities of MistNet NDR are powered by patent-pending TensorMist-AI™ technology, which uses distributed computing to scale data collection and analytics. This provides the ability to collect and enrich security data ‘on location’ generating exceptionally accurate behavioural and threat models without having to move any of the data.
LogRhythm’s SaaS delivery, combined with this mesh-network analytics processing, creates the ideal SaaS and data collection model that optimises scale and lowers operating costs.

Managed NDR – Service Features
EDGENETIC’s managed Network Detection and Response service provides the most highly accredited expertise combined with Gartner Magic Quadrant leading security technology to deliver industry-leading protection for your organisation.
Our approach is proactive, and threat led; informed by our offensive and threat intelligence teams to shape our defensive stance and protect against the latest industry threats, providing in-depth unrivalled detection and alerting capability where it is needed most.

Frequently Asked Questions about Data Privacy Security
What is an incident response policy?
An Incident response plan or policy is a process you create before you experience a cyberattack. This is so that your team has a procedure to follow when you do experience a data breach. EDGENETIC follows the CREST Cybersecurity Incident Response process which is broken down into 3 phases: preparation, response, and follow up. Having a breach plan gives you the confidence to quickly nullify any threat to your data privacy security.
Why is data privacy security important?
Although it has always been important, the implications and need for higher security are coming into play now that technology is indispensable to everyday life. Using apps, browsing websites, and shopping online are all examples of how your data will be stored and managed online. For organisations today, the threat of cyber theft is a pertinent one. Having comprehensive data privacy plans in place can reduce and mitigate the risks of such events.
Does EDGENETIC practice sustainability?
As a company with a global footprint, sustainability is an area of importance to us. We are a registered ‘Investor in People’ organisation. Taking a cue from ISO 14001, we have strong sustainability practices put in place. Our organisation also hires fairly and equally, across gender and race. By working with us, you can rest assured that we implement data privacy security measures with ethics at the core of our mission.
