MANAGED CLOUD PROTECT
Controlling your Cloud environments
The EDGENETIC Managed Cloud Protect service deploys next-generation cloud compliance and security monitoring suite provided by Check Point CloudGuard to provide advanced visibility, oversight, and control for your cloud environments. This is integrated into the EDGENETIC global SOC and Aperture cyber operations platform to provide you with 24/7/365 alerting and visibility.
EDGENETIC is an award-winning cybersecurity organisation with unparalleled capability in delivering managed security services. Through our global Security Operations Centres (SOCs) we provide round the clock cloud security monitoring services that secure our clients and detect and respond to sophisticated cyber-threats, providing assurance that your organisation is protected.
What Is Managed Cloud Protect?
EDGENETIC’s Managed Cloud Protect service is a cloud monitoring service that provides 100% visibility into your cloud estate. The service can be configured to protect the cloud environment and prevent misconfigurations – the primary cause of data loss. Taking control of the native cloud tooling enables a coherent and proactive security posture to be applied across the entirety of a clients cloud estate – visible and configurable from a single interface. This minimises the attack surface, protects against vulnerabilities, and identifies theft and data loss.
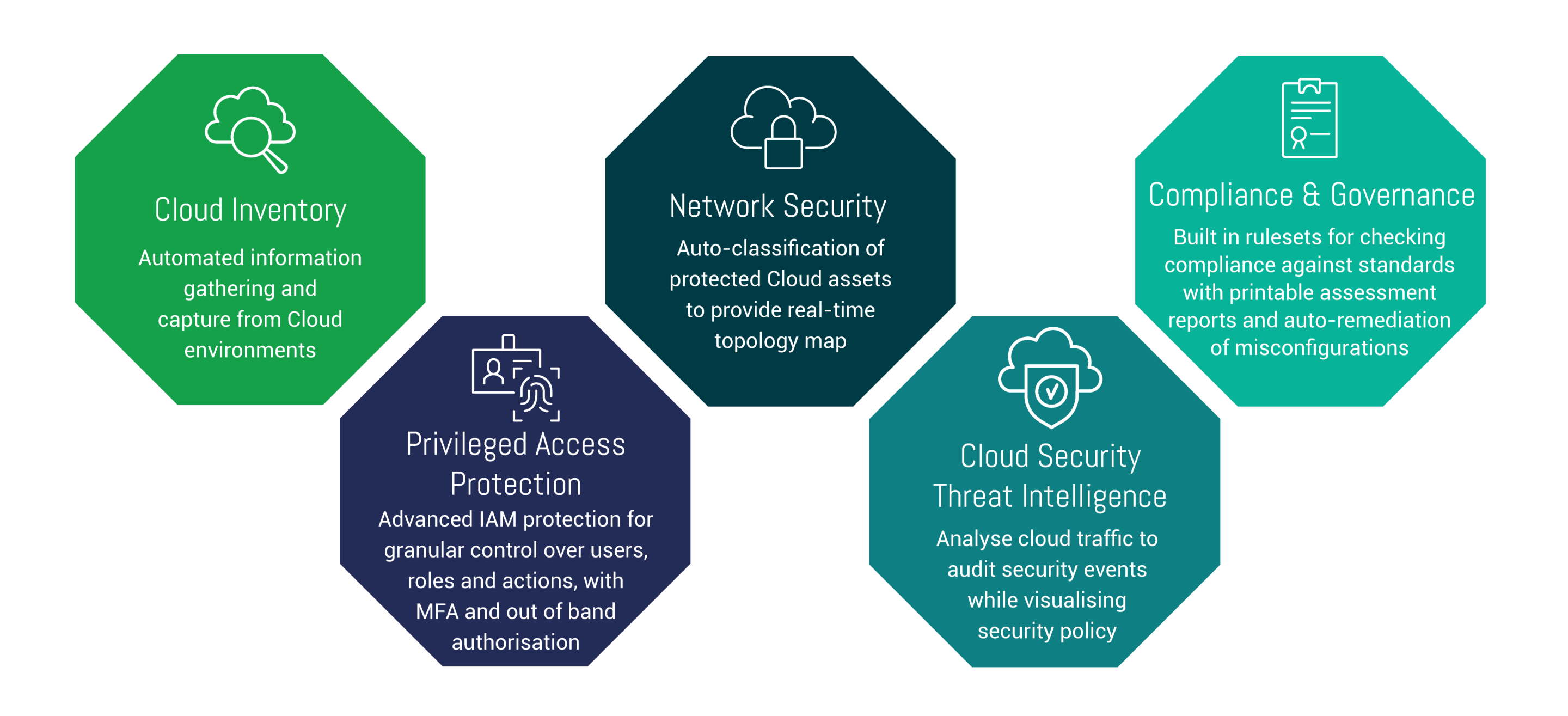
The service uses the industry-leading Check Point CloudGuard product suite. The solution comprises network security, application and workload protection, posture management, and cloud intelligence. The core product, CloudGuard Posture Management, assesses and visualises security posture, identifies misconfigurations, and can automatically enforce policies and protect against internal and external threats.
It also comes with Cloud Intelligence Essentials, a security monitoring system that utilises a combination of signature detection, built-in rules, and threat intelligence feeds to create a baseline of account activity. Unauthorised or malicious activity across cloud environments, including serverless applications, is detected by AI and anomaly detection algorithms. This provides real-time detection and prevention.
Automatic remediation is also possible using CloudBot technology. This can be used to deal with any type of network alert, audit issue, or threat, resolving dangerous misconfigurations and putting the environment back into compliance.
The Cloud Protect service will significantly reduce the likelihood of a misconfiguration leading to a data breach, as well as the time to detect and respond to an incident. These metrics (known as Mean Time to Detect or MTTD and Mean Time to Respond or MTTR) are key indicators of an effective detect and respond capability.
Benefits Of Managed Cloud Protect
Using Check Point CloudGuard, organisations can visualise and assess their security posture, detect misconfigurations, model, and enforce best practices, and protect against identity theft and data loss. CloudGuard integrates with Amazon Web Services, Microsoft Azure, and Google Cloud. Through a single dashboard, you will be able to achieve the following across your entire cloud estate:
- Easy security and compliance management of public cloud environments
- Top security standards with auto-remediation of unauthorised changes
- Spot misconfigurations quickly and easily, potentially preventing exposure of data
- Compliance with best practices by spotting misconfigurations in real-time
- Real-time privileged elevation for AWS users
- Auto-remediation of dangerous misconfigurations, saving on overheads and time
- Provide user activity analytics, network traffic visualisation, and intrusion detection
- Deny changes to network security groups, preventing unauthorised changes
- Granular visibility and control of users’ activities over native controls
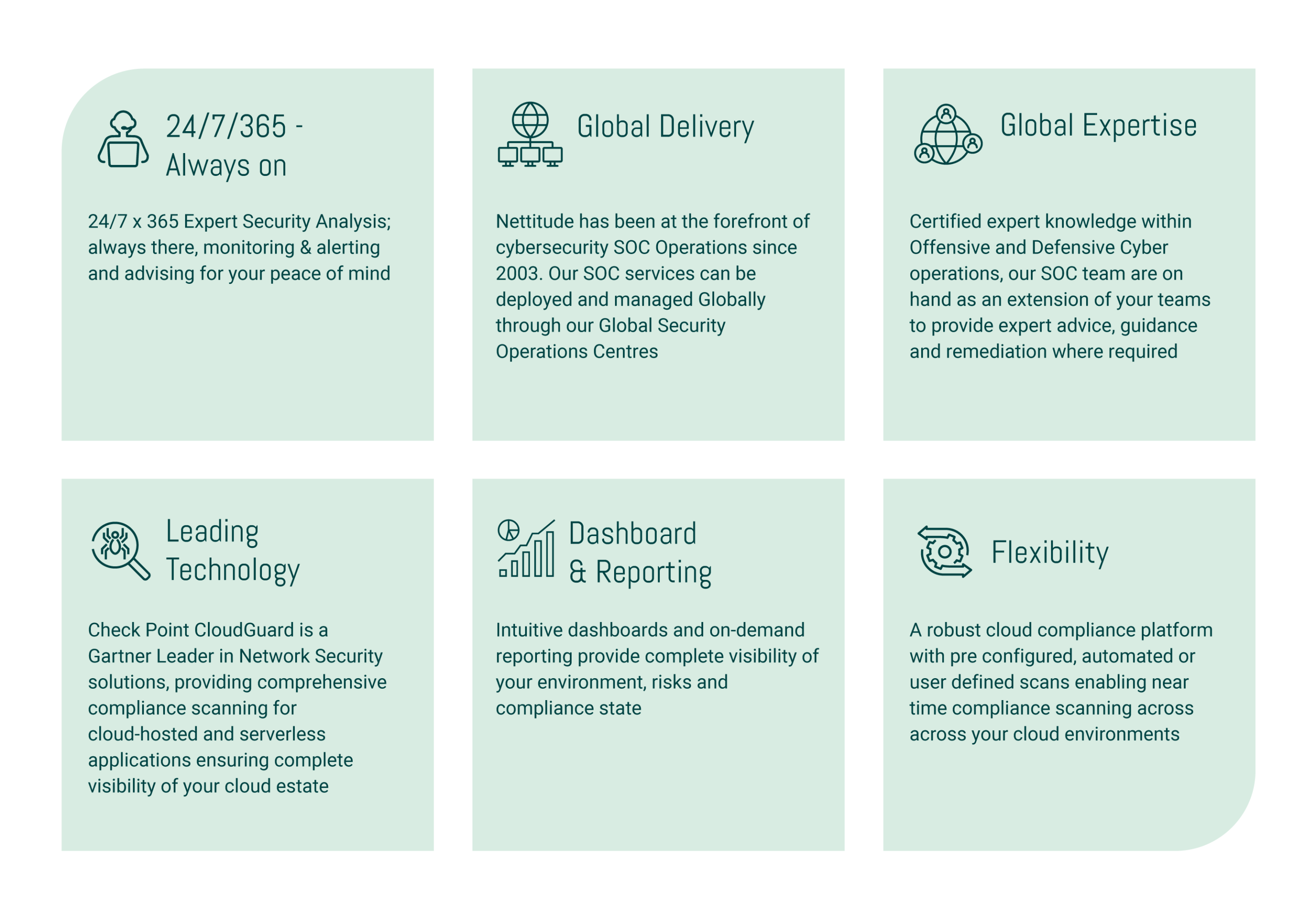
Managed Cloud Protect – Service Features
EDGENETIC’s Managed Cloud Protect service provides the most highly accredited expertise combined with Gartner Magic Quadrant leading security technology to deliver industry-leading protection for your organisation.
Our approach is proactive, and threat led; informed by our offensive and threat intelligence teams to shape our defensive stance and protect against the latest industry threats, providing in-depth unrivalled detection and alerting capability where it is needed most.
Frequently Asked Questions about Data Privacy Security
What is an incident response policy?
An Incident response plan or policy is a process you create before you experience a cyberattack. This is so that your team has a procedure to follow when you do experience a data breach. EDGENETIC follows the CREST Cybersecurity Incident Response process which is broken down into 3 phases: preparation, response, and follow up. Having a breach plan gives you the confidence to quickly nullify any threat to your data privacy security.
Why is data privacy security important?
Although it has always been important, the implications and need for higher security are coming into play now that technology is indispensable to everyday life. Using apps, browsing websites, and shopping online are all examples of how your data will be stored and managed online. For organisations today, the threat of cyber theft is a pertinent one. Having comprehensive data privacy plans in place can reduce and mitigate the risks of such events.
Does EDGENETIC practice sustainability?
As a company with a global footprint, sustainability is an area of importance to us. We are a registered ‘Investor in People’ organisation. Taking a cue from ISO 14001, we have strong sustainability practices put in place. Our organisation also hires fairly and equally, across gender and race. By working with us, you can rest assured that we implement data privacy security measures with ethics at the core of our mission.
